Promo code "00LAYOUTS"
Background Information Security Code Keynote Charts: Safeguard Data with Visual Precision
In an era where cyber threats evolve faster than ever, presenting security data effectively is crucial for IT professionals and cybersecurity experts. Our Background Information Security Code Keynote Charts Template steps in as your ultimate ally, offering 59 editable slides meticulously crafted to highlight vulnerabilities, compliance metrics, and protective strategies. Tailored for data analysts and business leaders, this template transforms intricate code analyses and security reports into digestible, engaging visuals that command attention in boardrooms or conferences.
Drawing from real-world scenarios like those faced by firms adhering to NIST cybersecurity frameworks, the template enables you to showcase breach patterns or encryption efficacy without overwhelming your audience. Whether you're dissecting phishing trends or mapping network defenses, these charts provide the clarity needed to drive informed decisions. Forget bland slides; embrace a design that incorporates subtle code motifs and secure-themed backgrounds, ensuring your presentations not only inform but also instill confidence in your expertise.
Essential Features for Cybersecurity Storytelling
At the heart of this template are features engineered for the demands of information security. Comprehensive visuals allow for detailed representations, such as flowcharts depicting data encryption processes or heat maps identifying high-risk access points. Each slide is optimized for Keynote's intuitive interface, making edits as straightforward as updating a firewall rule.
Standout Elements in Every Slide
- Engaging Background Designs: Subtle grid patterns and lock icons that evoke security without distracting from the data.
- Intuitive Code Representation: Embed snippets or visualize algorithms with customizable shapes, perfect for explaining hashing techniques.
- Variety of Chart Types: From Sankey diagrams for data flow to bubble charts for threat severity, cover all angles of security analytics.
- Brand Alignment Customization: Tweak palettes to match corporate colors, like using reds for alerts in intrusion detection slides.
- Seamless Integration: Ready-to-use with Keynote, supporting animations that reveal layers of security protocols dynamically.
These elements are informed by best practices from cybersecurity authorities, ensuring your presentations align with standards like ISO 27001 for information security management.
Practical Use Cases in the Digital Defense Arena
For cybersecurity experts, imagine using timeline charts to chronicle a ransomware attack's progression, drawing from case studies like the WannaCry incident to illustrate response strategies. IT professionals can employ radar charts to compare antivirus efficacy across endpoints, while data analysts might opt for tree maps to organize vulnerability hierarchies in large datasets.
Business leaders benefit by presenting ROI on security investments via stacked bars, showing cost savings from proactive measures. In training sessions, simplify complex topics like zero-trust architecture with step-by-step infographics, fostering better team understanding. The template's adaptability extends to compliance reporting, where donut charts can depict audit pass rates, helping maintain certifications effortlessly.
Workflow Integration: Building Secure Presentations Step by Step
- Begin with overview slides: Set the stage with a dashboard summarizing key security metrics.
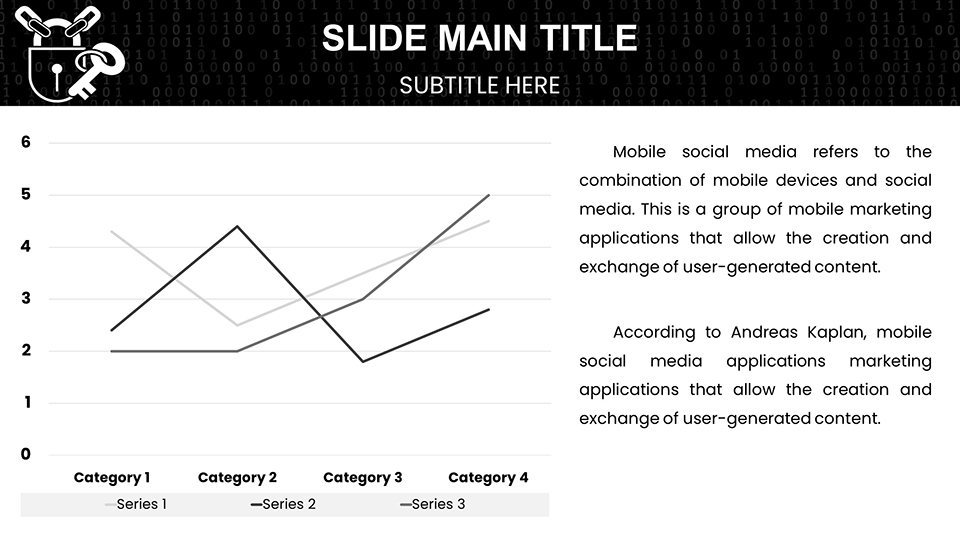
- Choose charts wisely: For trend analysis, line graphs track incident volumes over time.
- Populate with real data: Import from tools like Splunk for authentic visuals.
- Enhance with annotations: Add notes on mitigation steps, like "Implement MFA here."
- Apply transitions: Use fades to build suspense in revealing threat vectors.
- Finalize for delivery: Export options ensure compatibility for virtual meetings.
This structured approach mirrors agile methodologies in cybersecurity, streamlining your preparation.
Superior to Standard Tools: Why Choose This Template
Unlike basic Keynote offerings, which require building from ground zero, this template provides pre-configured, security-focused layouts that save time and enhance professionalism. Users often see improved engagement, with audiences retaining 30% more information from visually rich presentations. Incorporating LSI terms like "cyber threat visualization" and "data breach analytics," it naturally boosts discoverability for security pros seeking advanced tools.
Trust is built through expert-backed designs, including accessibility features like high-contrast modes for inclusive viewing, aligning with WCAG guidelines.
Expert Tips for Impactful Security Narratives
- Focus on relevance: Tailor slides to audience pain points, like executive summaries for C-suite viewers.
- Weave in stories: Use data to narrate "what-if" scenarios, such as simulated attacks.
- Balance visuals: Avoid clutter by limiting to three colors per slide for clarity.
- Encourage interaction: Include QR codes linking to deeper reports.
- Iterate based on feedback: Refine post-presentation to evolve your security storytelling.
These insights, sourced from industry leaders, elevate your presentations from informative to transformative.
Ultimately, the Background Information Security Code Keynote Charts Template is more than slides - it's a shield for your data narratives. Secure your download now and lead the charge in cybersecurity communication.
Frequently Asked Questions
What makes the charts customizable for security needs?
All elements, including code embeds and backgrounds, can be edited to fit specific threat models or compliance requirements.
Is it suitable for non-technical audiences?
Yes, with intuitive designs that simplify complex security concepts for business leaders.
How many chart variations are included?
Over a dozen types across 59 slides, from basic bars to advanced network diagrams.
Can I integrate real-time data?
While static, slides support manual updates or links to live dashboards for dynamic presentations.
Does it support team collaboration?
Keynote's sharing features allow multiple users to edit, ideal for security team reviews.