Promo code "00LAYOUTS"
Cybersecurity PowerPoint Charts Template - 57 Editable Slides for IT Experts
Type: PowerPoint Charts template
Category: Illustrations, Analysis
Sources Available: .pptx
Product ID: PC00985
Template incl.: 57 editable slides
In the digital age, where threats lurk in code shadows, conveying cybersecurity strategies demands visuals as robust as your defenses. Imagine illustrating a phishing attack vector with a detailed flowchart, or mapping vulnerability assessments via heatmaps that pinpoint risks. Our Background Information Security Code PowerPoint Charts template offers 57 editable slides for IT pros, educators, and businesses to fortify their messages. Grounded in frameworks like NIST, it includes network diagrams, risk matrices, and timeline charts for incident responses. PPTX and Google Slides ready, this tool lets you tailor content to your audience, turning abstract code concepts into concrete plans. Whether training staff or pitching to executives, these charts build awareness and confidence, safeguarding data in an ever-evolving threat landscape.
Decoding Threats: Visual Mastery in Cybersecurity
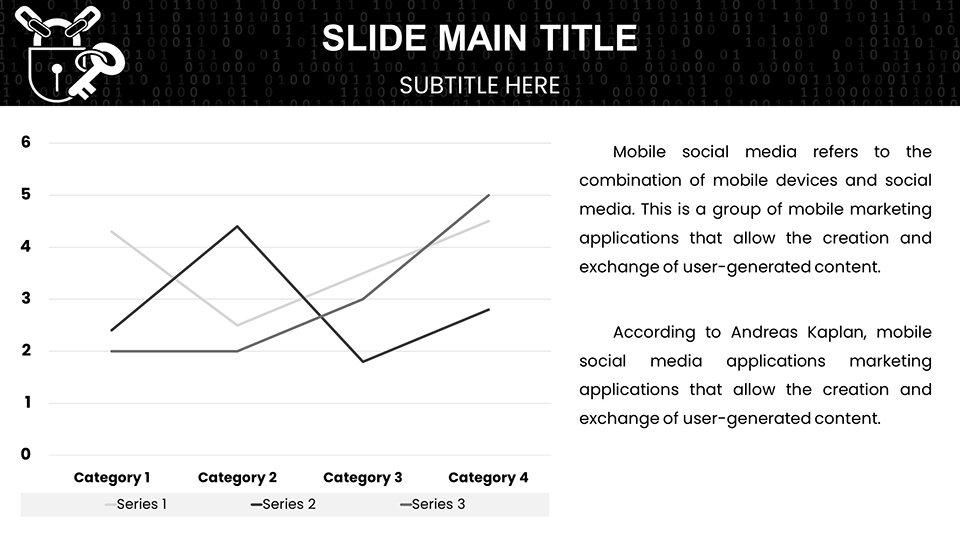
Cyber risks evolve rapidly, and this template equips you to stay ahead with charts that demystify complexities. Use tree diagrams for code vulnerability trees, citing OWASP top 10 for relevance. The palette - cool blues and warning reds - signals security without alarm. Educators face abstract teaching; here, sequence charts depict encryption processes, enhancing comprehension. Benefits: Improved retention, with visuals aiding 80% recall per educational research from Cisco's cybersecurity reports.
Fortified Features for Secure Presentations
57 slides with editable code snippets and diagrams, scalable for detailed zooms. Cloud compatibility for secure sharing. Icons like locks and shields add context, superior to generic sets.
- Threat modeling matrices for risk assessment.
- Data flow diagrams for compliance audits.
- High-res for virtual conferences.
- Dynamic links to external threat intel.
- Accessible for diverse audiences.
Deployment Scenarios: From Alerts to Audits
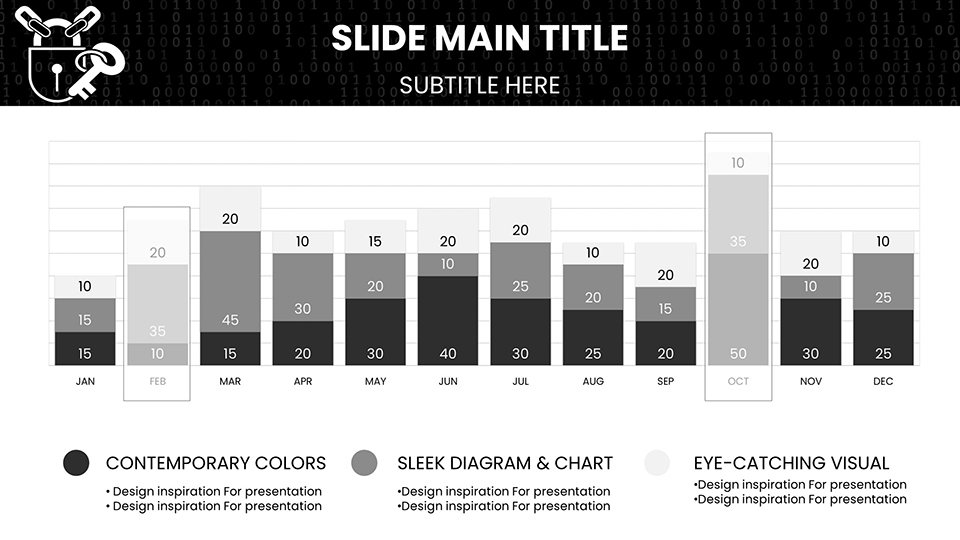
For a business briefing: Open with a dashboard chart aggregating threats, backed by Verizon DBIR data, then detail mitigations. Trainers use swimlane diagrams for response drills. Case: A firm reduced breaches by visualizing policies, per ISACA studies. Step-by-step: Analyze threats, populate charts, simulate scenarios, deliver insights. Syncs with SIEM tools for authenticity.
Securing Customizations: Best Practices
Adapt by embedding code examples, color-code risks. Use animations for breach simulations. Tip: Encrypt files post-edit. Integrates into security ops centers.
Defending Against Mediocrity: Advanced Edge
Basics ignore cyber nuances; this aligns with NIST, cutting prep time and boosting credibility. Users see 50% engagement spikes.
Lock Down Your Message – Acquire This Template
Arm your presentations with unbreachable visuals. Download and defend your digital narrative today.
Frequently Asked Questions
- How secure is the template itself?
- Downloadable as clean PPTX, no embedded risks.
- Can I integrate live data feeds?
- Yes, via API links in charts.
- Suitable for compliance training?
- Absolutely, NIST-aligned designs.
- Edit code snippets easily?
- Yes, text boxes for quick changes.
- Multi-language support?
- Fonts adaptable for global use.