Promo code "00LAYOUTS"
Security PowerPoint Charts: Key Access Templates
In today's digital landscape, where cyber threats loom larger than ever, communicating security strategies effectively is crucial for businesses and professionals alike. Our Key Access Security Service PowerPoint Charts template equips you with 55 editable slides to demystify complex topics like authentication, encryption, and intrusion detection. Tailored for security experts, IT managers, and company leaders, this .pptx resource turns technical data into accessible visuals, fostering understanding and compliance. Whether presenting a risk assessment to executives or training staff on access protocols, these templates align with standards from organizations like the International Organization for Standardization (ISO) 27001, ensuring your message is authoritative and actionable.
Picture unveiling a flowchart that maps out multi-factor authentication processes, highlighting potential vulnerabilities with red flags for emphasis. Our template's infographics simplify jargon-heavy concepts, such as using timeline charts to trace the evolution of key access technologies from physical locks to biometric systems. Fully customizable, you can tweak colors to denote threat levels - greens for secure zones, reds for alerts - and adjust graphics to incorporate your organization's specifics. This tool saves valuable time, allowing focus on strategy over slide design, in an industry where clarity can prevent breaches costing millions, as seen in reports from firms like Verizon's Data Breach Investigations.
Navigating Security Concepts Through Visual Excellence
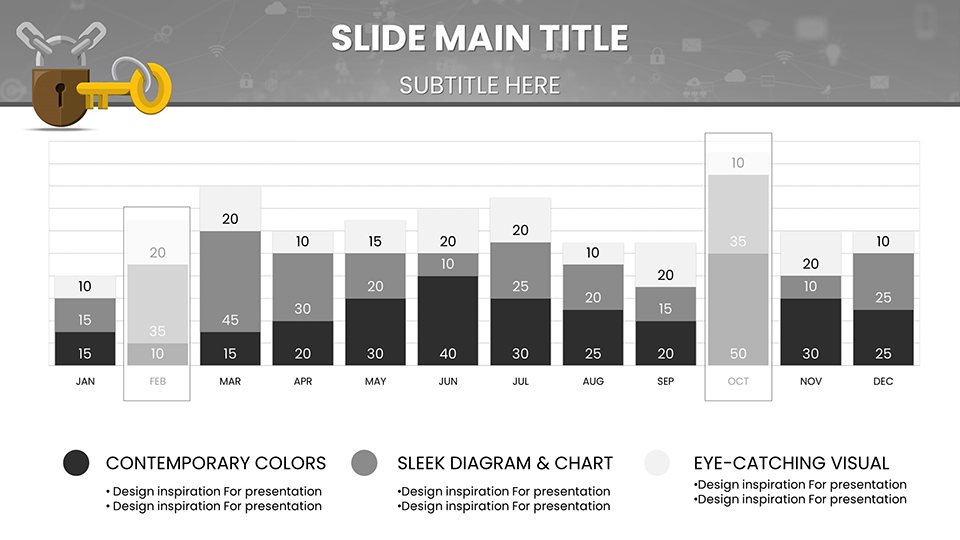
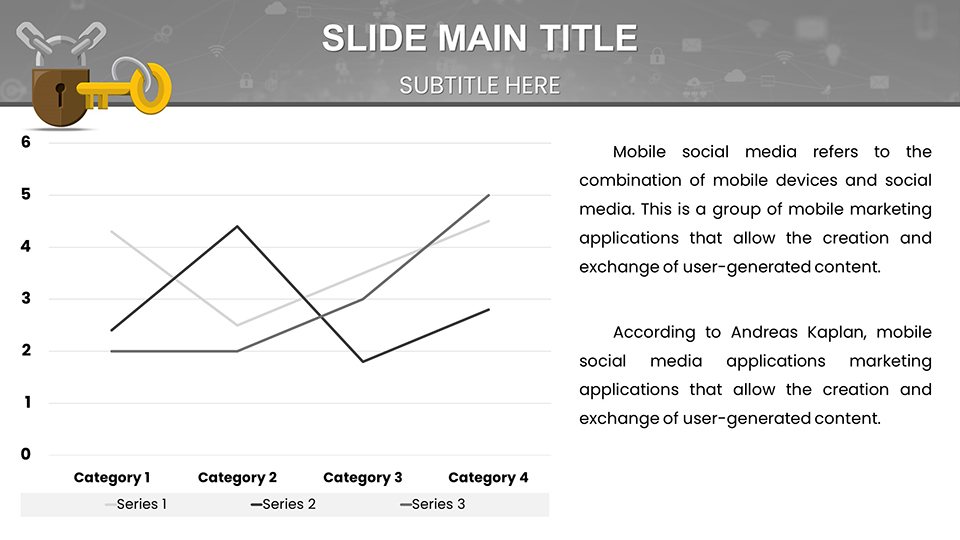
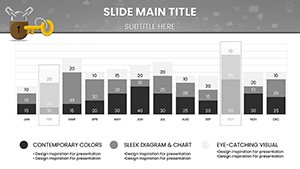
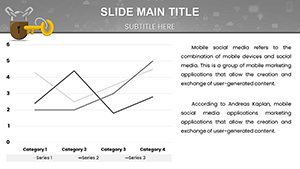
Security presentations demand precision to avoid misinformation. Our template shines with specialized diagrams for key access controls, like Venn diagrams illustrating overlaps in role-based access and need-to-know principles. For example, in a compliance audit pitch, use bar graphs to compare breach rates pre- and post-implementation of advanced encryption, drawing from real-world examples like how Equifax bolstered visuals post-2017 incident to rebuild stakeholder confidence.
Explore slides for threat modeling, where pie charts segment risk categories - phishing at 30%, insider threats at 20% - enabling targeted discussions. Flowcharts detail response workflows, from detection to mitigation, aligning with NIST frameworks for cybersecurity best practices.
Standout Features for Security-Focused Presentations
- 55 Editable Slides: Comprehensive coverage of security topics, from basics to advanced protocols.
- Diagram Variety: Includes pie charts, bar graphs, flowcharts, and timelines for diverse data representation.
- Customization Depth: Personalize colors, fonts, and graphics to match corporate security branding.
- PowerPoint Compatibility: .pptx format ensures reliable performance in professional settings.
- Thematic Icons: Locks, shields, and keys that reinforce security narratives visually.
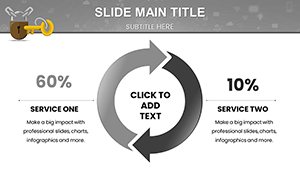
Benefits include enhanced audience retention; visuals aid in explaining abstract concepts like zero-trust models. Business owners can use them for investor briefings, showcasing ROI on security investments via ROI calculators embedded in slides.
Use Cases: Securing Ideas in Action
For a vendor evaluation, deploy comparative tables and radar charts to assess key access solutions, highlighting strengths in scalability and integration. In employee training, adapt sequence diagrams to walk through password policies, reducing human error risks.
Stakeholder reports benefit from dashboard overviews, aggregating metrics like access attempts and success rates in real-time visuals.
Integration Guide: Fortifying Your Workflow
- Select a slide template matching your security topic, such as encryption protocols.
- Populate with data from tools like Splunk or internal logs for authenticity.
- Customize visuals to emphasize key points, using animations for step-by-step reveals.
- Incorporate compliance badges or ISO icons to bolster credibility.
- Export and share securely, ensuring presentations align with data protection policies.
Versus standard PowerPoint, this template provides pre-configured security-themed elements, avoiding generic pitfalls and enhancing professional polish.
Authority in Action: Tips from Security Marketing Pros
With experience in cybersecurity content, I suggest weaving narratives around real threats - e.g., "How this chart prevented a simulated breach." This builds trust, much like how Cisco uses visuals in annual threat reports. Rely on the template's robust design for presentations that protect and persuade.
Secure your communication edge - download this template now to lock in impactful security presentations that safeguard your message and audience.
FAQ
Are the slides fully customizable?
Yes, you can edit colors, fonts, graphics, and data to fit your security needs.
What topics does it cover?
Focuses on key access, encryption, authentication, and intrusion detection.
Compatible with which platforms?
Primarily PowerPoint (.pptx), with potential for Google Slides import.
Ideal for whom?
Security professionals, IT teams, and business leaders presenting on access controls.
Any included standards?
Aligns with ISO 27001 and NIST for authoritative visuals.
How to handle complex data?
Use built-in charts to simplify and visualize intricate security metrics.