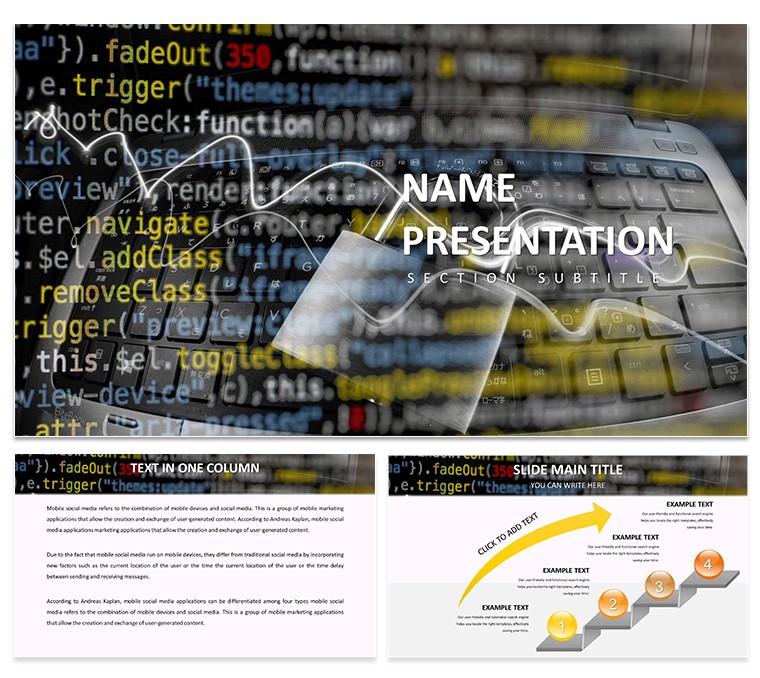
In today's hyper-connected world, cybersecurity isn't just a buzzword - it's a necessity. Envision presenting threat landscapes where your audience grasps the gravity of phishing attacks or ransomware without overwhelming jargon. This free Cybersecurity PowerPoint Template equips IT specialists, educators, and business leaders with 28 robust diagrams in 7 color schemes to do just that. Designed for clarity on topics like network protection and data encryption, it's fully editable and compatible with PowerPoint and Google Slides. Ideal for training sessions or risk assessments, it helps demystify cyber risks, promoting proactive strategies. Skip the bland defaults; opt for slides that convey urgency and solutions, drawing from frameworks like NIST to establish authority and trust in your delivery.
Navigating the Complexities of Cyber Threats
Cyber threats evolve rapidly, from malware to zero-day exploits. This template's visuals simplify these: use matrix diagrams for vulnerability assessments or tree structures for incident response plans. Editable charts allow integration of stats from sources like Cybersecurity Ventures, underscoring projected trillions in damages. For security analysts, illustrate firewall configurations with layered infographics, aligning with CIS Controls for best practices. This not only showcases expertise but reassures audiences of your grounded approach.
Essential Features for Secure Presentations
- Threat-Focused Diagrams: 28 slides depicting attack vectors, encryption models, and compliance checklists.
- Color Options: Seven schemes, including high-alert reds and secure blues, to emphasize risks.
- Crisp Graphics: Vector icons of locks, shields, and hackers for thematic relevance.
- Seamless Data Handling: Import breach data effortlessly for timely updates.
- Accessibility Built-In: Compliant designs for diverse audiences.
Addressing design pitfalls, these ensure your message on cyber hygiene lands effectively.
Applying the Template in Real Scenarios
For corporate training, use it to outline employee protocols against social engineering, with role-play scenarios via flowchart slides. Educators can teach ethical hacking basics, referencing cases like the Equifax breach illustrated in timeline formats. Startups benefit in compliance audits, presenting GDPR alignments through comparative tables. Awareness campaigns for nonprofits might highlight personal data protection, using pie charts on common vulnerabilities - echoing FBI cybercrime reports.
Customization Workflow for Cyber Experts
- Theme Selection: Pick a scheme to match your tone, like stark contrasts for warnings.
- Data Insertion: Fill in threat intel from reliable sources.
- Media Enhancement: Embed simulation videos or policy links.
- Layout Tweaks: Standardize with masters for professionalism.
- Delivery Prep: Animate breach sequences for dramatic effect.
This streamlines secure content creation.
Pro Tips from Security Veterans
Structure with storytelling: introduce threats, detail defenses, end with resilience strategies. Cite ISO 27001 standards for authority. Superior to basics with specialized pentest diagrams, as in Deloitte's cyber reports. In seminars, animations mimic attacks, boosting retention.
Superiority in Defense Visuals
Includes risk heat maps absent in generics, vital for boardroom decisions like CrowdStrike implementations.
Empower your cyber narratives today.
Secure Your Download and Strengthen Defenses
Fortify your presentations - download this free template to lead in cybersecurity discourse.
Frequently Asked Questions
How flexible are the security diagrams?
Completely editable for custom threat models.
Compatible with other software?
Yes, works with Google Slides and PowerPoint.
Good for training?
Perfect for interactive sessions on cyber awareness.
Formats provided?
.pptx, .potx, .jpg included.
Usage limits?
Free for all purposes, unlimited edits.