Envision unveiling a threat landscape where binary streams morph into shield barriers, data flows guarded by lock icons - your audience leans in, grasping vulnerabilities without jargon overload. The Background Information Security Code PowerPoint template arms IT pros, compliance officers, and cybersecurity firms with this edge, delivering 28 diagrams that decode digital defenses into digestible visuals. It's for those boardroom briefings where risks run high and clarity is your cipher.
Styled in a dark canvas pierced by electric green highlights - echoing code matrices and alert glows - this template exudes tech-savvy tension. Three masters anchor layouts, three backgrounds toggle from matrix overlays to clean voids, suiting from C-suite summaries to dev team deep dives. Core to its code: Placeholders for threat models, icon sets for encryption layers, and charts plotting breach trends, all vector-sharp for zoom-proof precision.
In a field where threats evolve overnight, this template future-proofs your pitches. Embed audit logs into timelines, animate firewall flows to simulate attacks, or radial-map user access hierarchies. It's about empowerment - turning tech talk into trusted tactics, much like how firms like those in NIST frameworks use visuals to align strategies. Secure your spotlight; let's breach the basics.
Core Defenses: Features That Encrypt Excellence
Like layered security, this template's three masters multi-factor your design, applying themes that shield inconsistencies. Backgrounds adapt - subtle code for intros, bold grids for metrics - ensuring your deck decrypts smoothly.
Diagrams as Digital Shields
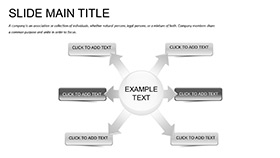
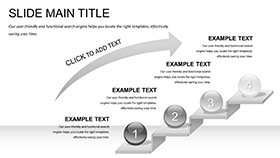
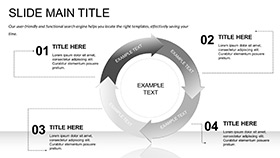
Twenty-eight diagrams fortify your flow: Network topologies in Venn overlaps, risk matrices with heat-coded cells, and process maps tracing incident responses from detect to remediate.
- Threat Visuals: Funnel diagrams narrowing attack vectors, with icon stops at each safeguard.
- Data Flows: Sankey charts streaming info paths, highlighting bottlenecks like unpatched ports.
- Compliance Grids: Checkmatrix layouts for GDPR checklists, tickable via hyperlinks.
Seven schemes modulate intensity - neon for alerts, monochrome for reports - adapting to venue vibes.
Unlocking Edits with Master Keys
PowerPoint 2016+ compliant, .potx loads with editable paths: Recode colors in themes, script animations for phased reveals, or query external data for live phish stats.
Key: Layer transparency on overlays, mimicking data veils - ideal for revealing phased protections.
Threat Simulations: Use Cases in Action
Cyber talks demand drama; this template scripts it. For a quarterly review: Boot with a code-veiled title, agenda into vectors via a radar scan diagram, pulsing sectors for focus areas.
Protocol for a Security Audit Deck
- Scan Scope: Pinpoint topics - phishing drills or zero-trust models.
- Map Mitigations: Tree diagrams branching defenses, leaves as tactics like MFA.
- Metric Shields: Gauge dials for vulnerability scores, needled to baselines.
- Case Cracks: Timeline breaches with before icons, post with fortified symbols.
- Lockdown Legacy: Action matrix assigning owners, deadlines in progress bars.
Such sequencing, akin to CERT protocols, clarifies countermeasures, often hardening policies post-pitch.
Training and Trend Tracking
For workshops, sequence sims animate exploits, pausing for Q&A. Trends track in line surges, spiking on incidents with callout warnings.
Beating blanks, its binary motifs avoid blandness, where plain pies pale - here, streams symbolize stakes vividly.
Byte-Sized Boosts for Breach-Proof Talks
Path animate cascades for cascade failures, alts like "Binary code background with green lock overlay" for access. Integrate SIEM feeds for dynamic threats, refreshing sans reloads.
A CISO leveraged the grids for role mappings, streamlining access audits. Precision like this patches persuasion gaps.
Code Your Confidence Now
For guardians of the grid, this template is your vault. Acquire for $22 and armor your arguments. Defend the deck - download today.
Frequently Asked Questions
Compatibility details?
Works with PowerPoint 2016+, supporting animations and links across platforms.
Editing binary elements?
Vectors allow recolor and reshape; swap for custom code snippets.
Icon variety?
Security-themed set included; expand via insert for specifics like VPNs.
Data visualization support?
Charts link to Excel for auto-updates on metrics like uptime.
Dark mode benefits?
Reduces eye strain in low-light, enhances green accents for focus.