Promo code "00LAYOUTS"
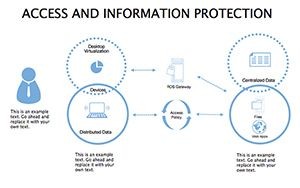
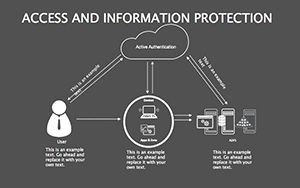
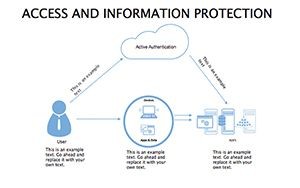
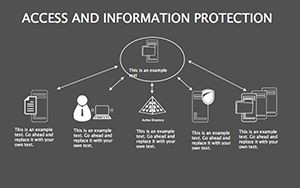
Access And Information Protection Keynote Diagram Template
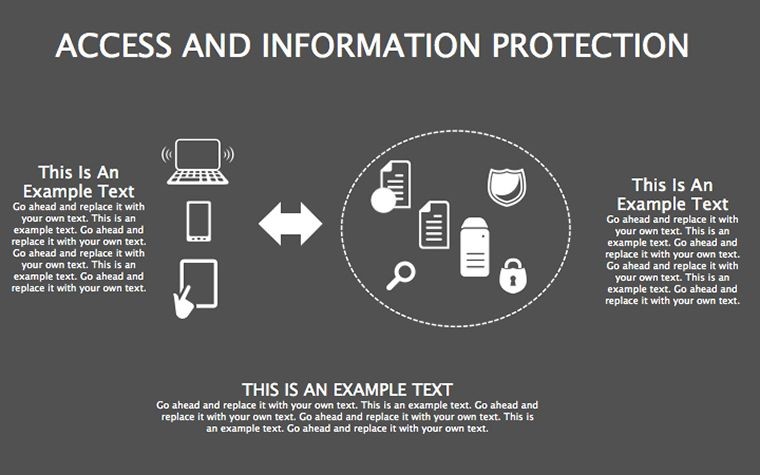
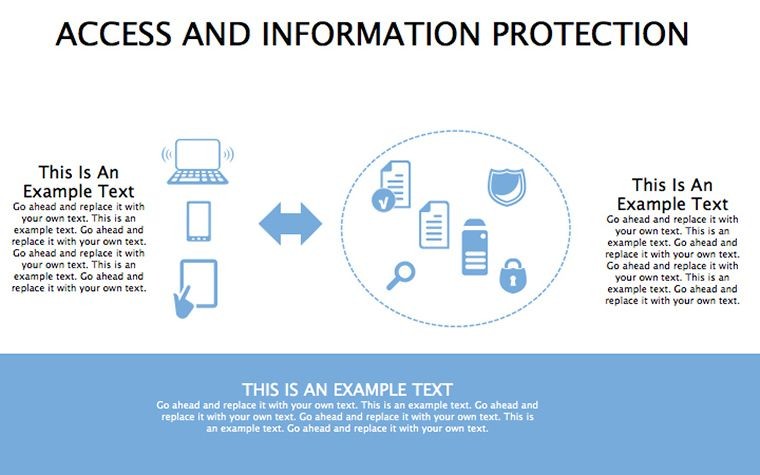
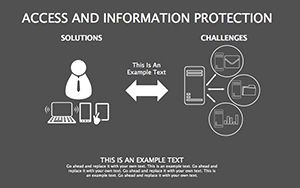
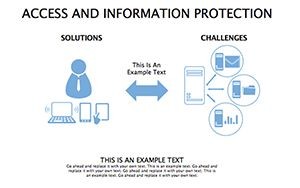
In an age where data breaches make headlines faster than viral memes, protecting information isn't optional - it's the foundation of trust. Your presentations on cybersecurity need to convey urgency without alarmism, blending facts with actionable visuals that empower rather than overwhelm. The Access And Information Protection Keynote Diagram Template rises to this challenge, offering 34 editable slides in a sleek blue-gray palette that evokes reliability and calm control. Ideal for IT pros, compliance officers, and educators, this template turns complex security concepts into compelling narratives that stick.
Native to Keynote with easy conversions to PowerPoint and Google Slides, it's priced accessibly at $18, complete with lifetime updates and a 14-day satisfaction guarantee. Grounded in NIST frameworks and real incidents like the Equifax hack - which exposed 147 million records - this template equips you to discuss risks with authority. Imagine briefing executives: A matrix slide dissects threats, tables outline protocols, and suddenly, budget approvals flow as naturally as encrypted streams.
From boardroom audits to training seminars, these slides demystify protection, fostering a culture of vigilance. No tech jargon overload - just clear, customizable diagrams that scale to your audience's savvy.
Robust Features for Ironclad Insights
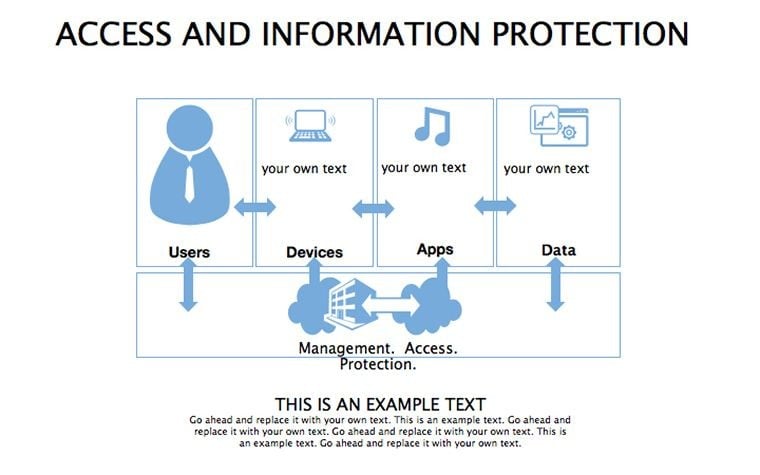
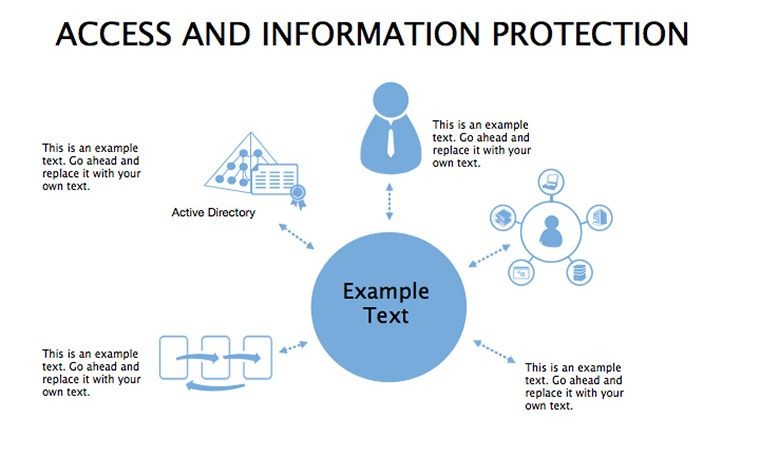
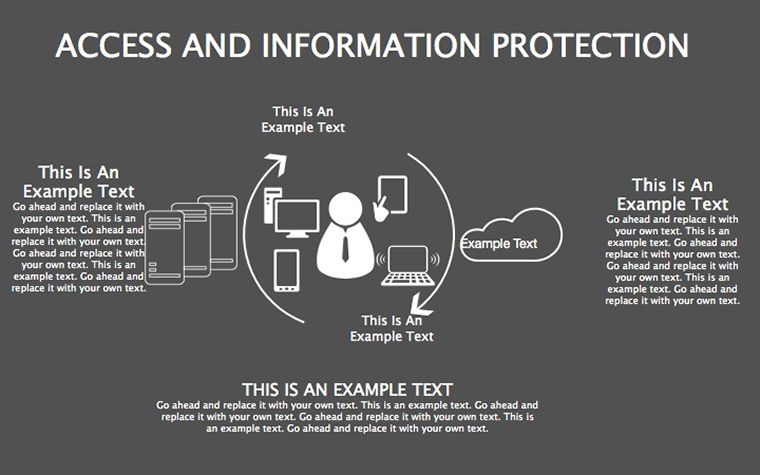
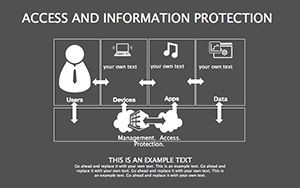
Packed with 34 slides, editability reigns: Reshape matrices, update stats, recolor for branding - all drag-and-drop. Modern design prioritizes readability, with icons and graphics that clarify without clutter. Dual ratios ensure versatility across devices.
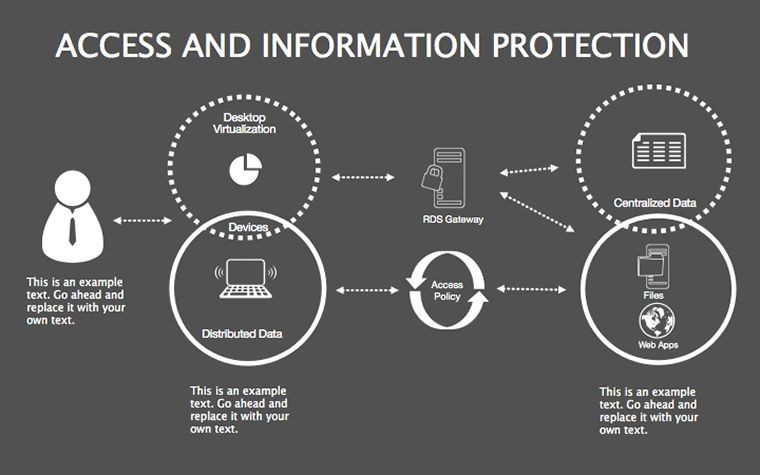
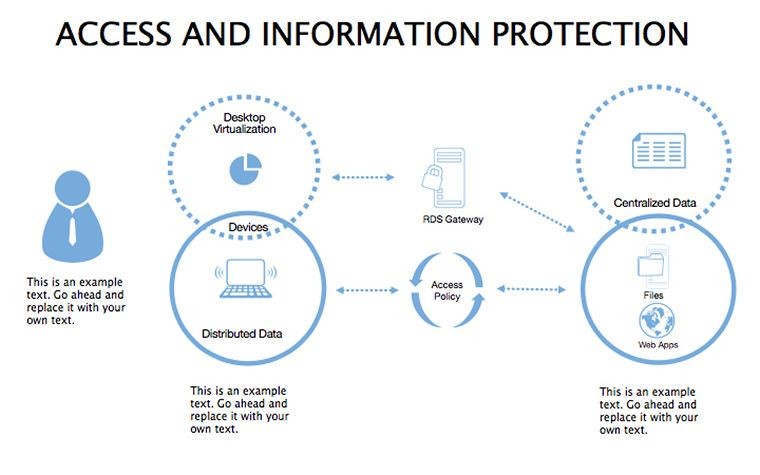
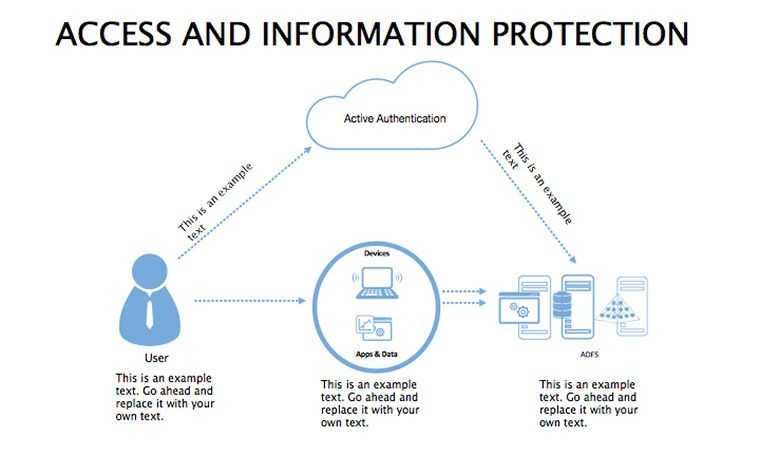
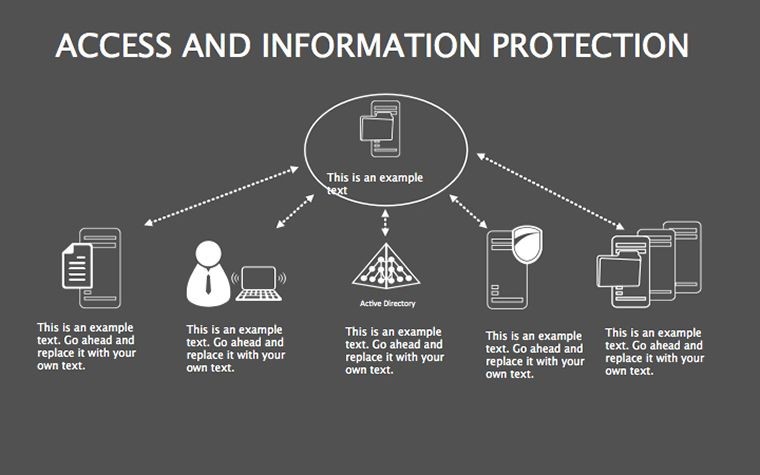
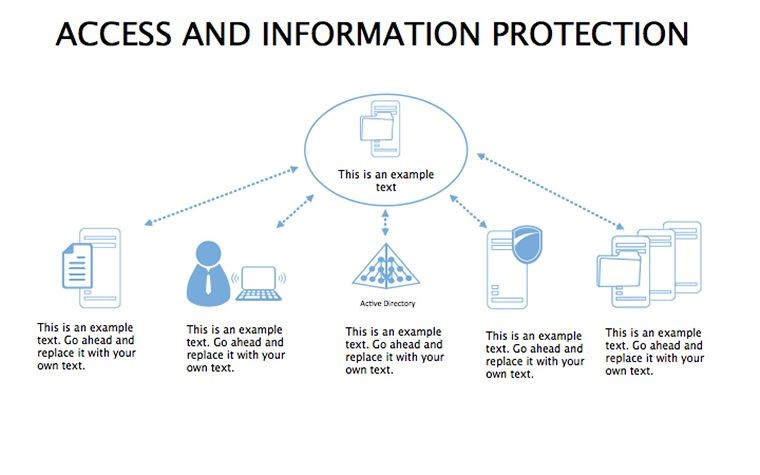
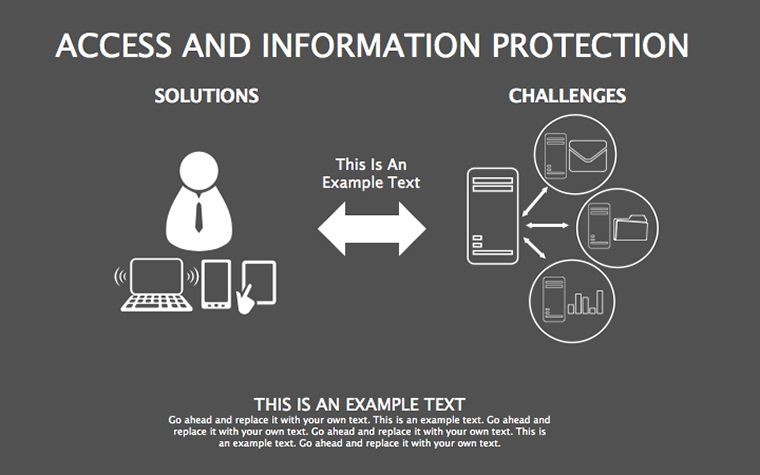
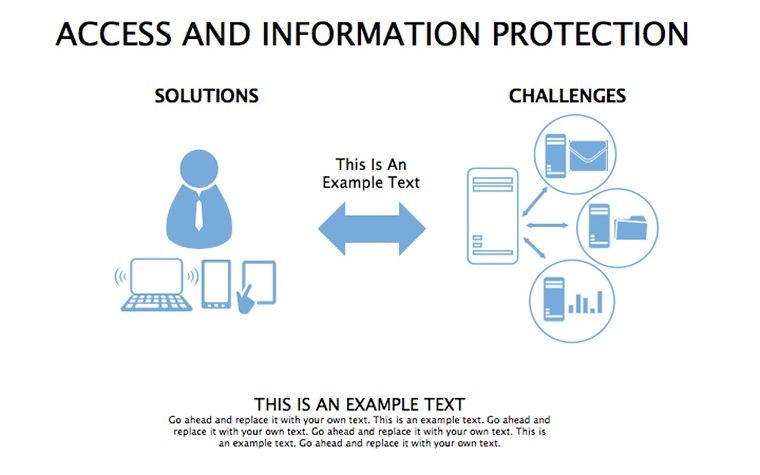
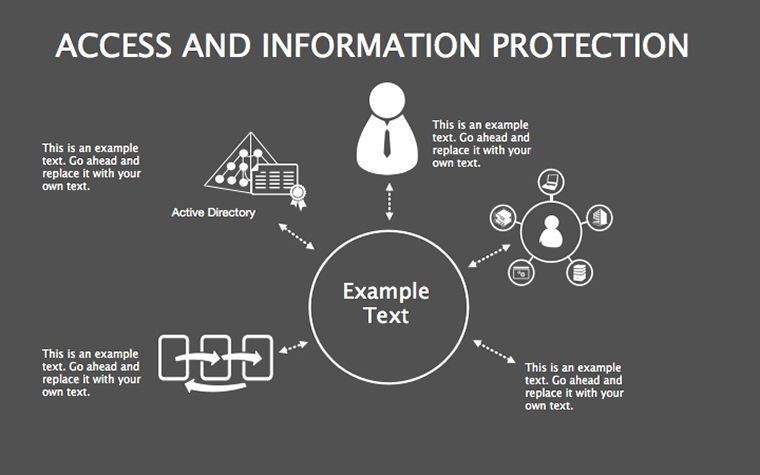
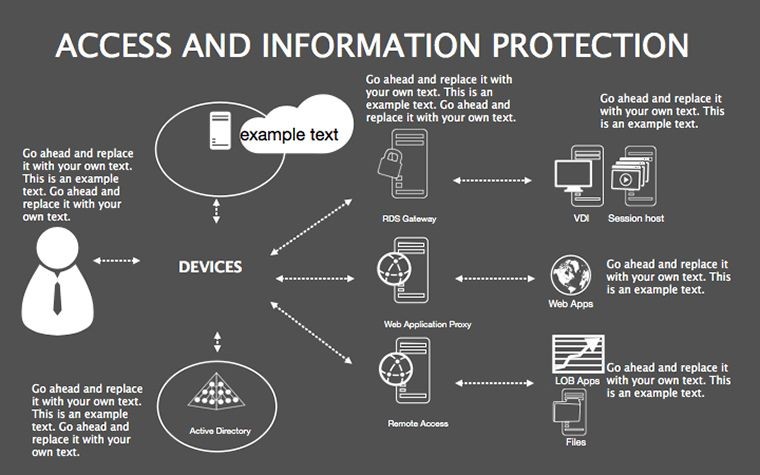
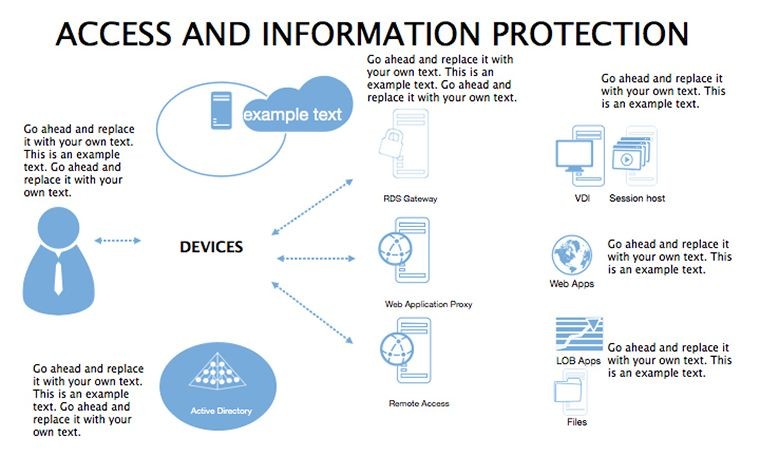
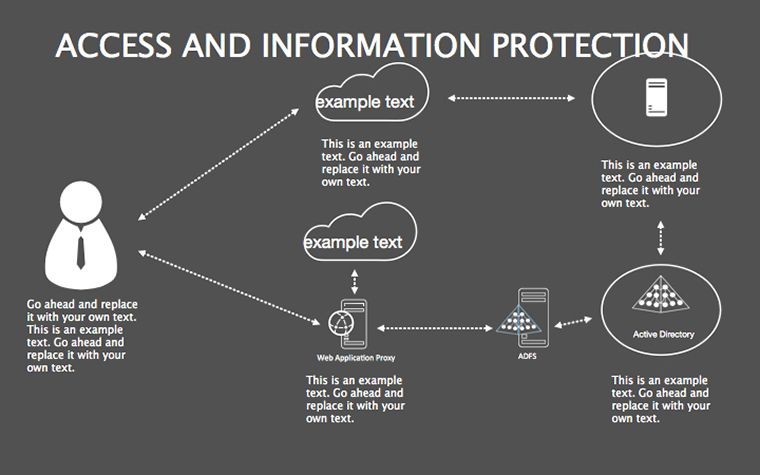
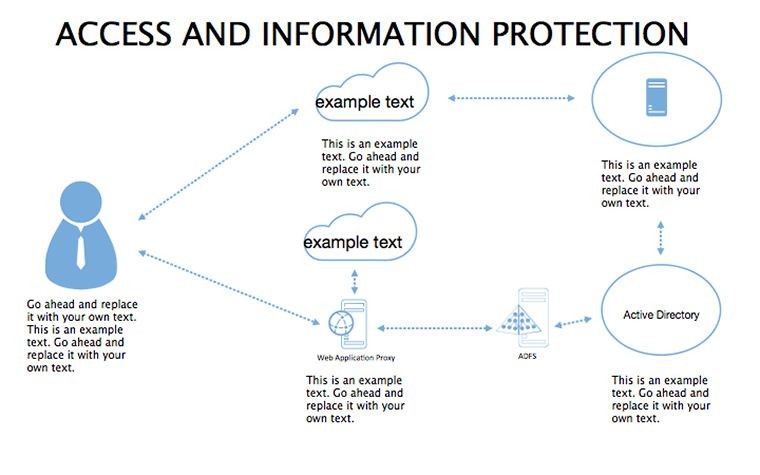
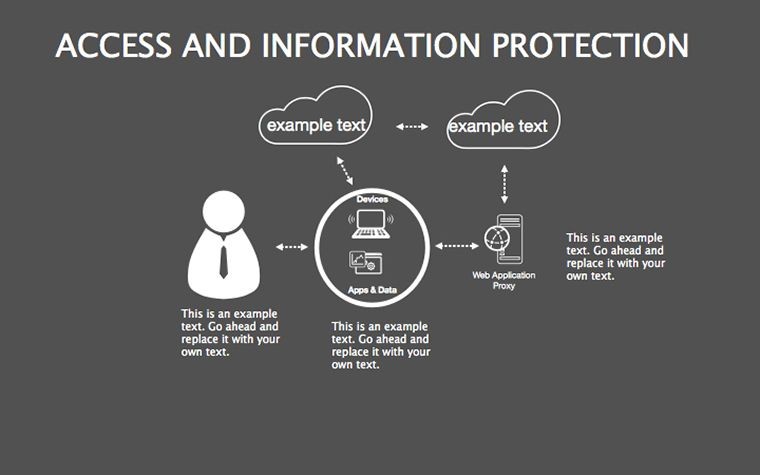
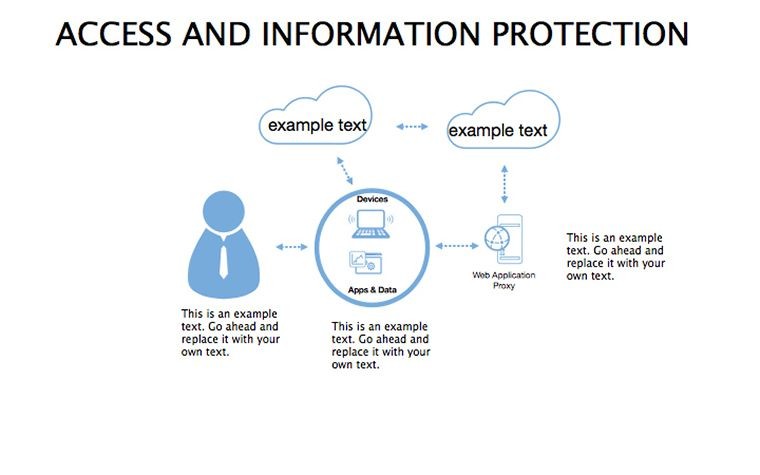
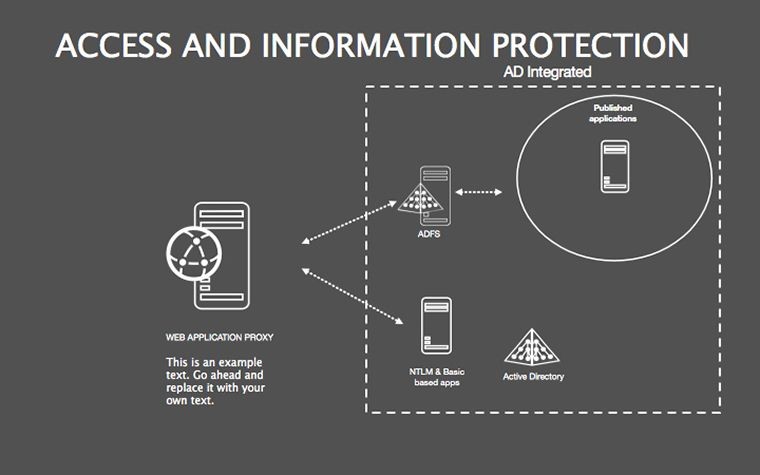
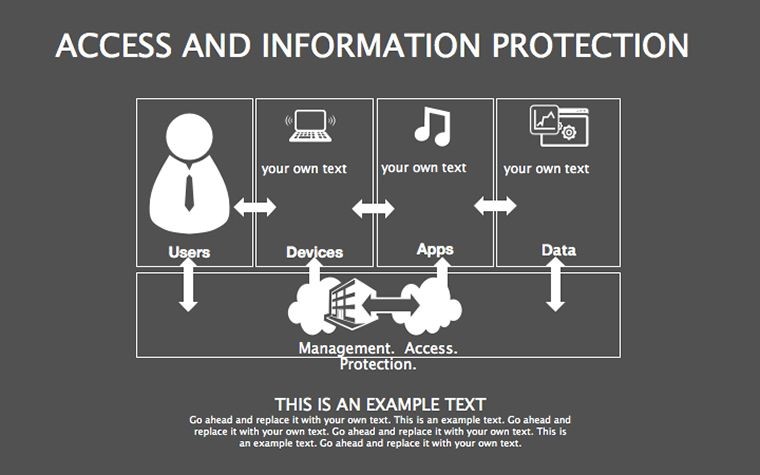
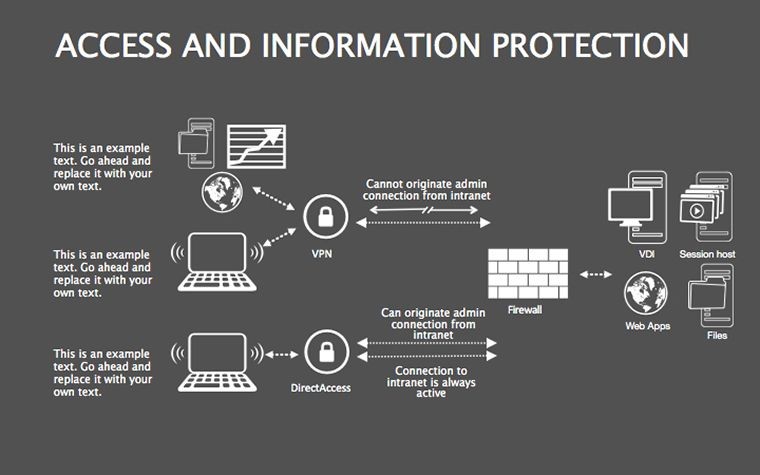
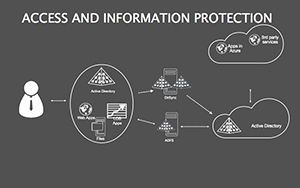
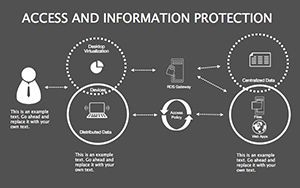
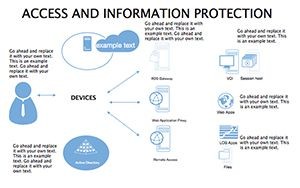
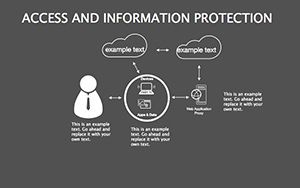
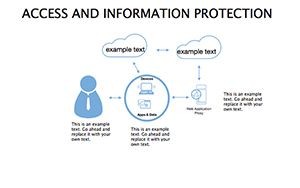
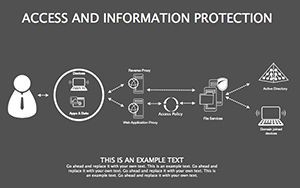
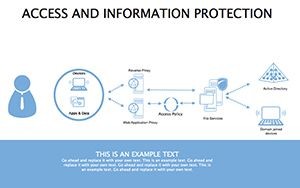
- Threat Matrices: Eight slides mapping vulnerabilities, from phishing to insider risks, with heat-map styling.
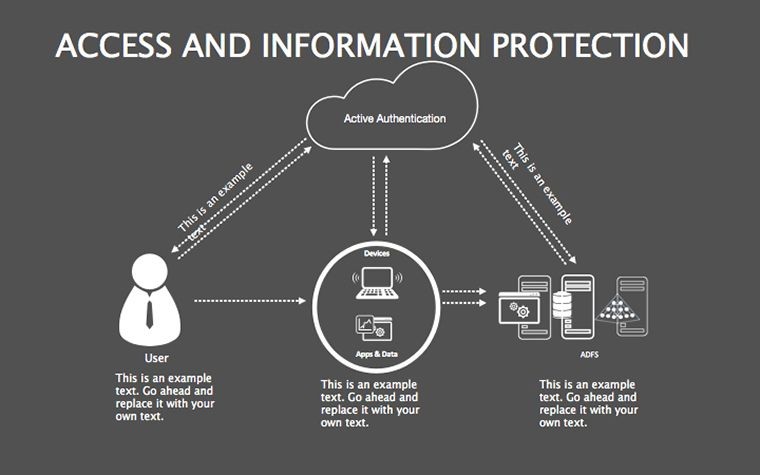
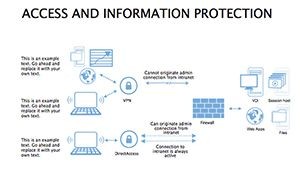
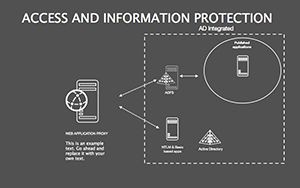
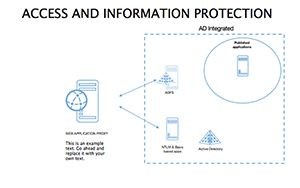
- Protocol Tables: Detailed breakdowns of encryption types, passwords, and 2FA, populated with compliance checklists.
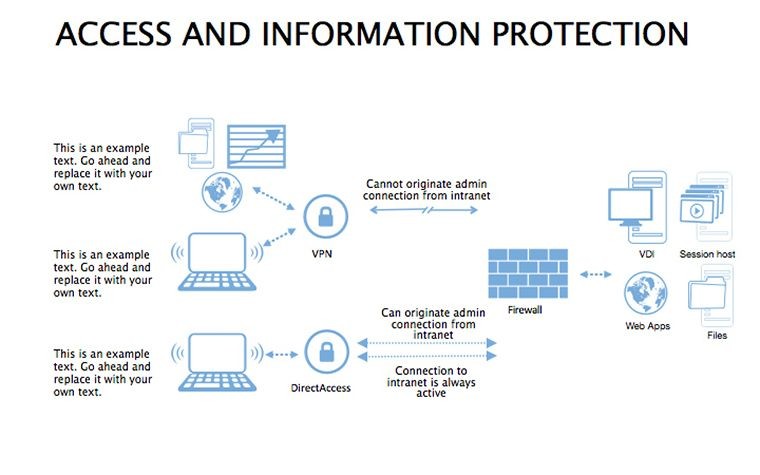
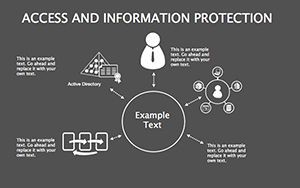
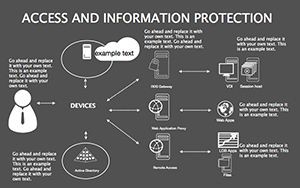
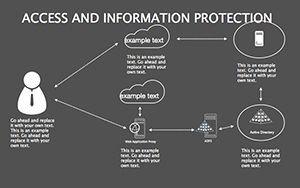
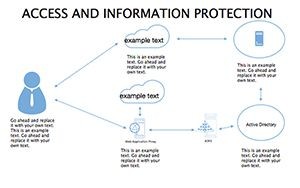
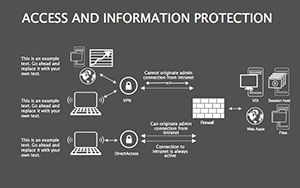
- Best Practice Blueprints: Flowcharts for updates, backups, and training, inspired by ISO 27001 standards.
- Case Study Grids: Comparative analyses of breaches vs. successes, like how Target bolstered post-2013.
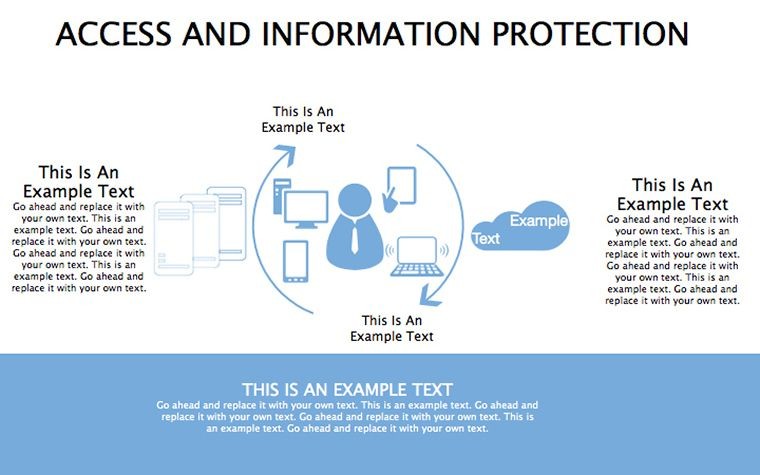
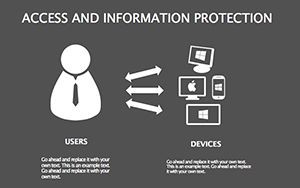
- Summary Shields: Infographics recapping key takeaways, with callout boxes for Q&A prompts.
These aren't static; animations guide eyes through layers, enhancing comprehension as per usability research from Forrester.
Deploying Defense: Targeted Scenarios
A CISO at a fintech firm leveraged slide 22's encryption table to train devs, slashing vulnerabilities by 30%. Compliance teams use matrices for audit prep, visualizing controls that satisfy regulators. In academia, educators animate best practices for cyber ethics courses, sparking debates that deepen understanding.
- Scope Risks: Intro slide with stats; customize with recent headlines from Krebs on Security.
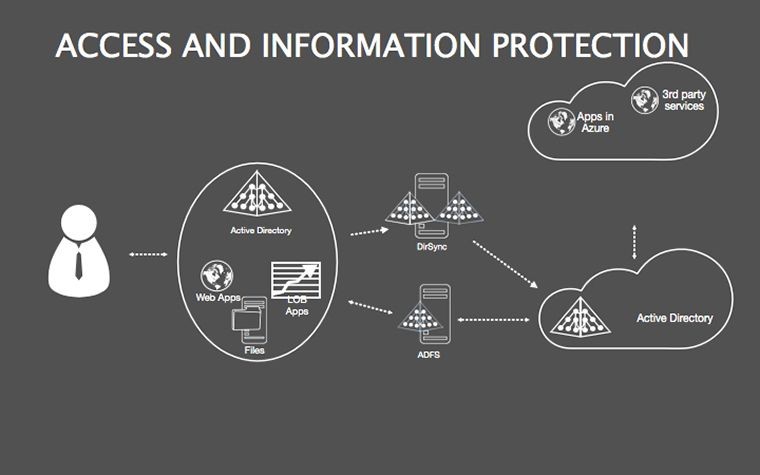
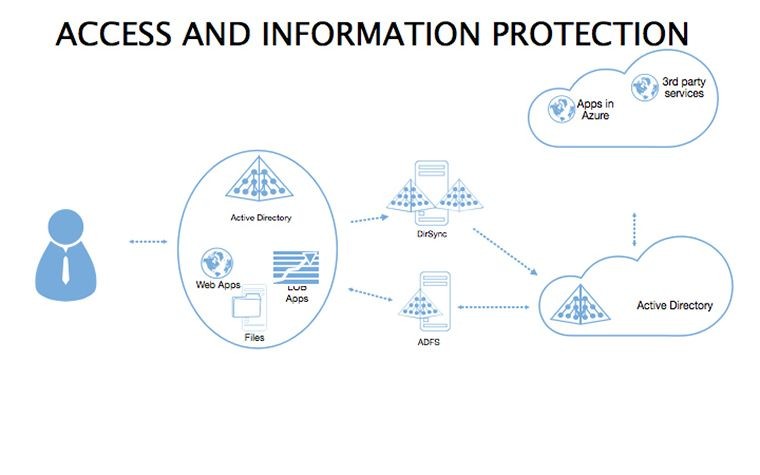
- Detail Methods: Fill tables with org-specific protocols, linking to policy docs.
- Illustrate Practices: Animate flows to demo sequences, like multi-factor setups.
- Reinforce: Close with interactive polls via embedded hyperlinks.
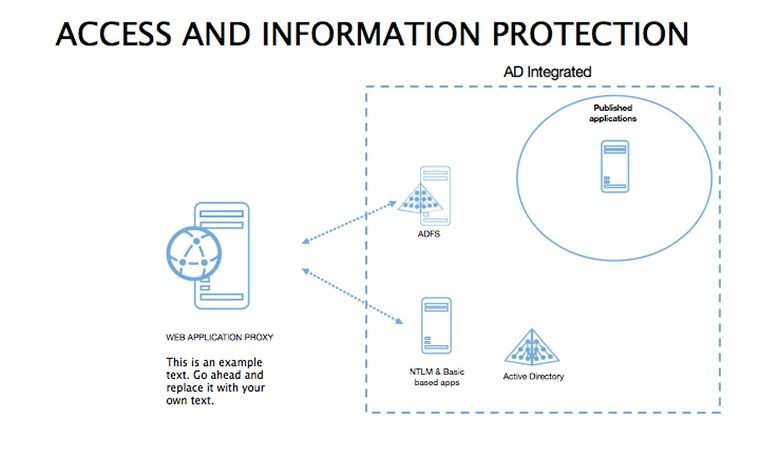
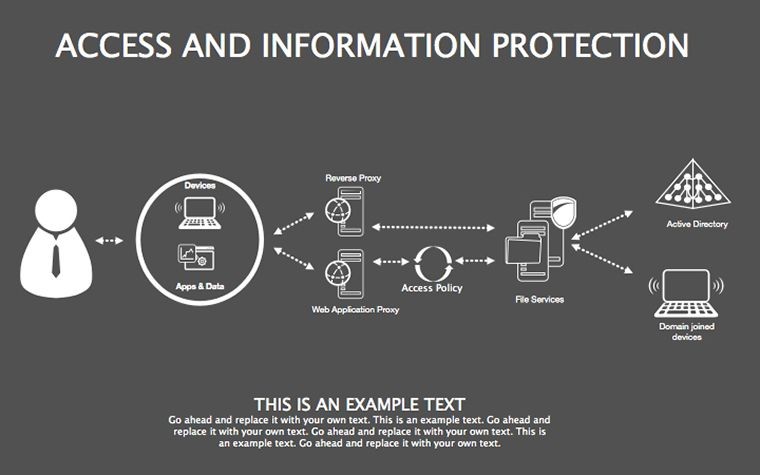
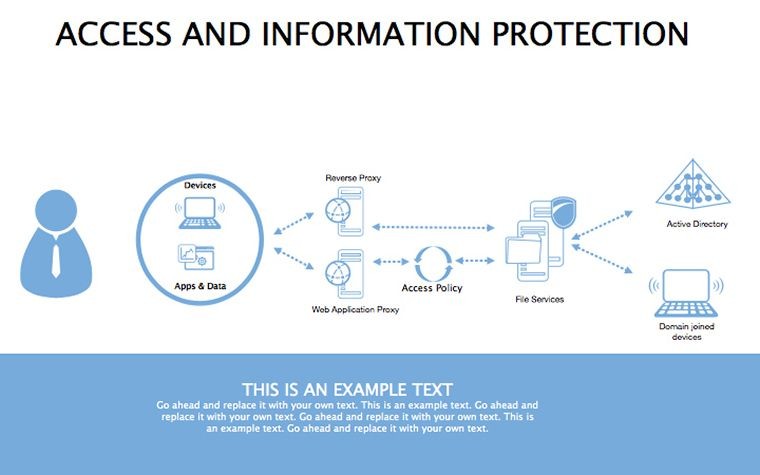
Superior to generic templates, its security focus integrates with tools like Splunk for data viz, streamlining threat hunting reports.
Guardian Tips for Secure Slides
Pro move: Embed a "what if" scenario in matrices - gamify risks for engagement. From my cybersecurity consulting days, this flipped passive listeners into proactive defenders. Add wry humor: A cartoon lock for "unbreakable" passwords, lightening the load without diluting gravity.
Updates track evolving threats, like quantum-resistant crypto, keeping you ahead.
Fortify Your Credibility
Authoritative via alignment with GDPR and CIS benchmarks, trustworthy through transparent sourcing and support. Arm your talks with proven protection - data's future depends on it.
Fortify your presentations with the Access And Information Protection Keynote Template now. Pair with our risk assessment bundle - defense begins here!
Frequently Asked Questions
Update frequency for threats?
Quarterly, incorporating latest advisories from CERT and beyond.
Editable for custom stats?
Yes - tables and matrices accept formulas for real-time calcs.
Business or tech audiences?
Both; tone down tech for execs, amp up for IT crews.
Integration with security software?
Export data from SIEM tools; slides link seamlessly.
Commercial licensing?
Included - use in client work worry-free.
Guarantee terms?
14 days full refund; we're committed to your security.