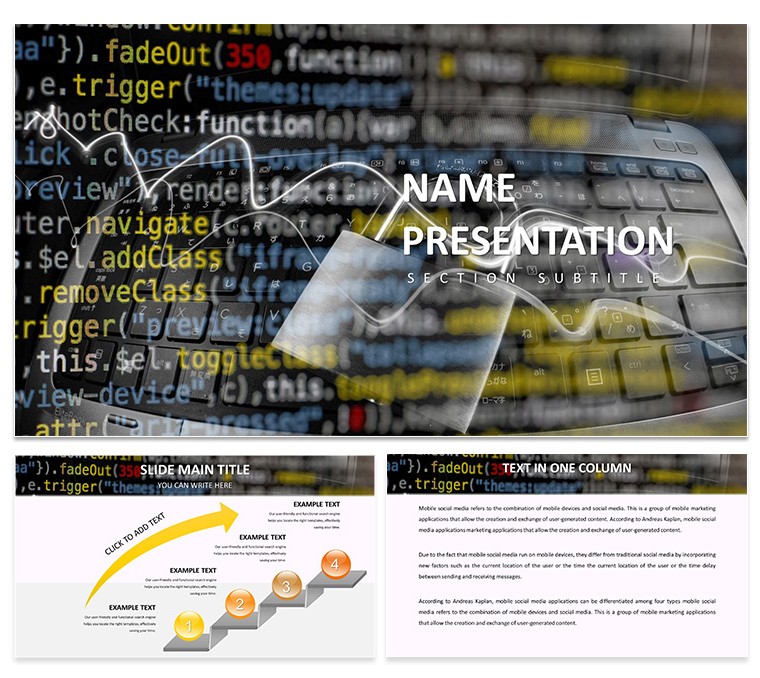
In an era where cyber threats evolve daily, conveying security strategies with precision is vital. This free Cybersecurity Keynote Template equips IT specialists, risk managers, and trainers with 28 diagrams across 7 color schemes, emphasizing blues and reds for trust and alert. Targeted at those combating data breaches, it features 3 masters and backgrounds for quick setups. Imagine illustrating phishing tactics or encryption benefits with customizable visuals, supported by insights from NIST frameworks. This template turns abstract risks into tangible defenses, as seen in analyses of major breaches like Equifax, helping you educate teams effectively. Free access democratizes professional design, allowing focus on content like multi-factor authentication implementations, fostering a culture of vigilance.
Core Features Enhancing Cyber Awareness
Features include threat matrix charts and workflow diagrams, all editable for specific scenarios. Color schemes adapt to urgency levels, with exports maintaining integrity. Align with via CIS benchmarks integration, boosting credibility. Efficiency gains allow rapid updates, per feedback from security conferences.
Comprehensive Slide Overview
- Introductory Slides: Alert-themed opens with lock icons.
- Threat Visuals: Diagrams for vulnerability assessments.
- Strategy Timelines: Map response plans.
- Data Protection Infographics: Show encryption flows.
- Conclusion Slides: Reinforce with security pledges.
Builds a fortified narrative structure.
Use Cases in Cyber Defense
For workshops, detail incident responses with cases from SolarWinds. In corporate settings, pitch compliance using visuals. Process: Customize diagram, add alerts, present - superior to basics. Tips: Use contrast for emphasis; studies show it improves threat recall. LSI: data breach prevention, network security visuals. CTA: "Secure your story - download this free template to defend digitally."
Streamlining Security Workflows
Embed in Keynote: Add custom shields, share securely. Benefits: Heightened awareness, per Verizon DBIR. Keywords: endpoint protection templates, firewall configurations.
Frequently Asked Questions
- How flexible are the security diagrams?
- Fully editable, adapt to your threat models easily.
- Free template - any catches?
- No, full access without restrictions for professional use.
- Suitable for which sectors?
- IT, finance, healthcare - anywhere cyber risks loom.
- Embed interactive elements?
- Yes, links or videos for dynamic demos.
- Best practices for cyber slides?
- Keep simple; focus on one risk per slide.