Conceive cloaking critical configs in clouds that command confidence - this Secure Cloud for Business Keynote Template is your vault for virtual valor. Tailored for sysadmins, CIOs, and cloud curators curating compliance constellations, it clouds 28 diagrams detailing from encryption envelopes to failover fortresses. Keynote-centric for crisp Mac renders, with broad-band exports, it's the shield shaping shadows into strategies.
Snapshot a security summit: Vanilla vaults vaporize as vault diagrams vault vulnerabilities, vaulting vigilance. Or an ops overhaul - redundancy rings ring resilience, ringing results resonantly. In cloud's chimeric challenges, diagrams demystify defenses decisively.
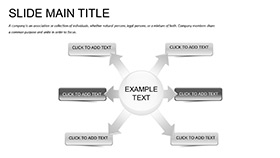
Bedrock Builds: The Cloud Compendium
Three masters mount your mainframes, three backgrounds blanket from byte blues to lock lavenders. 28 diagrams, seven schemes stout - from steel grays to guard greens - all vectors vaulting voids. Keys, clusters, and kiosks key into Keynote's kinetic kit.
- Fortress Forms: Flowcharts for firewall flows, matrices for multi-tenant matrices, arcs for access arcs.
- Yield Yields: Recode ranges for robust reveals, type tweaks for terse tomes.
- Sentry Slots: Spaces for SIEM snapshots, bonds to breach briefs.
Guardian gist: Glow guards gateways, glowing guardians guardedly.
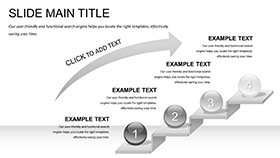
Deployment Domains: Clouds in Command
Audit assemblies assemble with access audits: Tier triangles triage threats, triaging trust transparently. DevOps dashboards deploy dependency digs, digging durability deeply. It's the bastion buttressing business bulwarks.
Migration memos map multi-cloud mazes, marking milestones meticulously. Vendor validations validate via Venns, vending veracity. These aren't adjuncts; they're anchors.
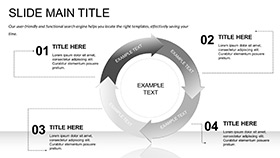
Schema for Securing Sessions
- Scan the Skyline: Survey scopes - safeguards, scales, safeguards.
- Stack the Shields: Stack a stack schematic; segment segments securely.
- Signal the Sentinels: Shade shades for severity scales, e.g., amber alerts ascending.
- Sequence the Surge: Surge surges sequentially, surging scrutiny.
- Solidify Shares: Spin for silos or syndicates, solidity sealed.
This schema steels speeches with strategic steel, succinct yet steadfast.
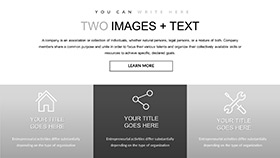
Fusing with Framework Frontiers
Prime pairing: Pins pin protocols, pinning pinches in pooled preps through ether edits. Schemes stretch spans for summit standards, outpacing plain pilots in prompt prowess. Flex fosters framework flips fleetly.
Distributed drills? Diminutive data darts dart deftly, driving distributed dialogues. Summits simulated solidly - swirl stacks spherically.
Fortifying with Frontier Fixtures
Fixture feast: Firewall fans for fanout flows, node nests for nested nodes - navigable via nodes. Builds like barrier broadcast barriers, barricading basics boldly. Logs latch lightly, linking to log lakes.
Text: Slab for specs, script for scripts - secure scansion.
Steward's Stratagems for Stalwart Slides
Pore over previews in panel, paring perils. Cryptic codes? Ciphers cipher cleanly, captions casual. Cadence: Controls commence, crises crest, closures cap - cascading convincingly.
Device diagnostics deliver durable designs. Vapor variants vault versatility, from vaults to virtuals.
Lock your ledger - land this for $22 and layer legacies.
Frequently Asked Questions
Adaptable for hybrid cloud hybrids?
Affirmative, architectures adapt adeptly, allying all arrangements.
Broad export breadth?
Broadly .pptx bridges, bridging 96% buoyant.
Scheme strength for diagrams?
Seven sentries, from somber to sentinel, singled singly.
Third-party tool ties?
Tether to Terraform or Twilio transparently, tying ties tightly.
Master metrics?
Three: Header harbor, body bastion, footer fort.
Enterprise endorsement?
Endorsed for exec exposés; escrow essentials.